Railway cybersecurity from ENISA, Nov. 2021
European railway undertakings and infrastructure managers systematically address cyber risks as part of their security risk management processes, especially after the Network and Information Security (NIS) Directive came into force in 2016. Addressing cyber risks in the railway sector can raise entirely new challenges for railway companies who often lack the internal expertise, organisational structure, processes or the resources to effectively assess and mitigate them.
The nature of railway operations and the interconnectedness of railway undertakings, infrastructure managers, and the supply chain requires all involved parties to achieve and maintain a baseline level of cybersecurity.
Directive 2016/1148 (NIS Directive) is the first legislative document focusing on cybersecurity in the EU. It identifies Operators of Essential Services (OES) in the railway sector as:
Infrastructure managers (IM), as defined in point (2) of Article 3 of Directive 2012/34/EU, include: “any person or firm responsible in particular for establishing, managing and maintaining railway infrastructure, including traffic management and control-command and signalling. The functions of the infrastructure manager on a network or part of a network may be allocated to different bodies or firms”.
Railway undertakings (RU), as defined in point (1) of Article 3 of Directive 2012/34/EU, include: “any public or private undertaking licensed according to this Directive, the principal business of which is to provide services for the transport of goods and/or passengers by rail with a requirement that the undertaking ensures traction. This also includes undertakings which provide traction only”. This also includes operators of service facilities as defined in point (12) of Article 3 of Directive 2012/34/EU as “any public or private entity responsible for managing one or more service facilities or supplying one or more services to railway undertakings”.
The NIS Directive requires IMs and RUs to conduct risk assessments that “cover all operations including the security and resilience of network and information systems”. According to the NIS Directive, these risk assessments, along with the implementation of appropriate mitigation measures, should promote “a culture of risk management” to be developed through “appropriate regulatory requirements and voluntary industry practices”. This need for cyber risk management in the European railway sector was also identified as a key priority by the participants of the ENISA-ERA conference “Cybersecurity in Railways”, which took place online on 16-17 March 2021 and brought together more than 600 experts from railway organisations, policy, industry, research, standardisation, and certification.
While some EU Member States (MS) have issued relevant national guidance to OESs on how to conduct cyber risk assessments, most railway operators choose to adopt one of the different methodologies introduced by industry standards. Indeed, there are currently varying approaches to tackle risk in the railway sector and for now, there is no single approach that covers both information technology (IT) and operational technology (OT) cyber risks.
Cyber-Related Threats
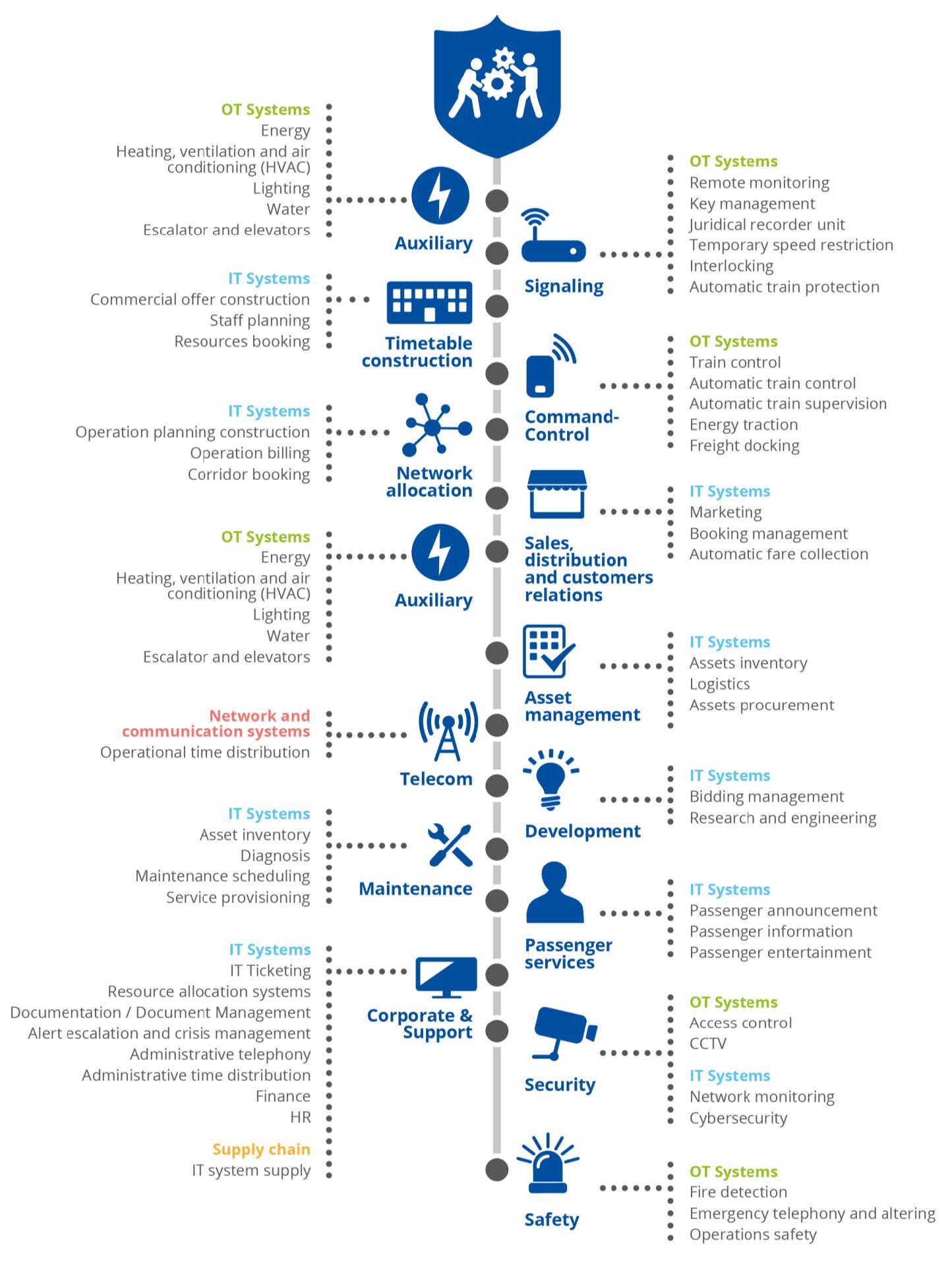
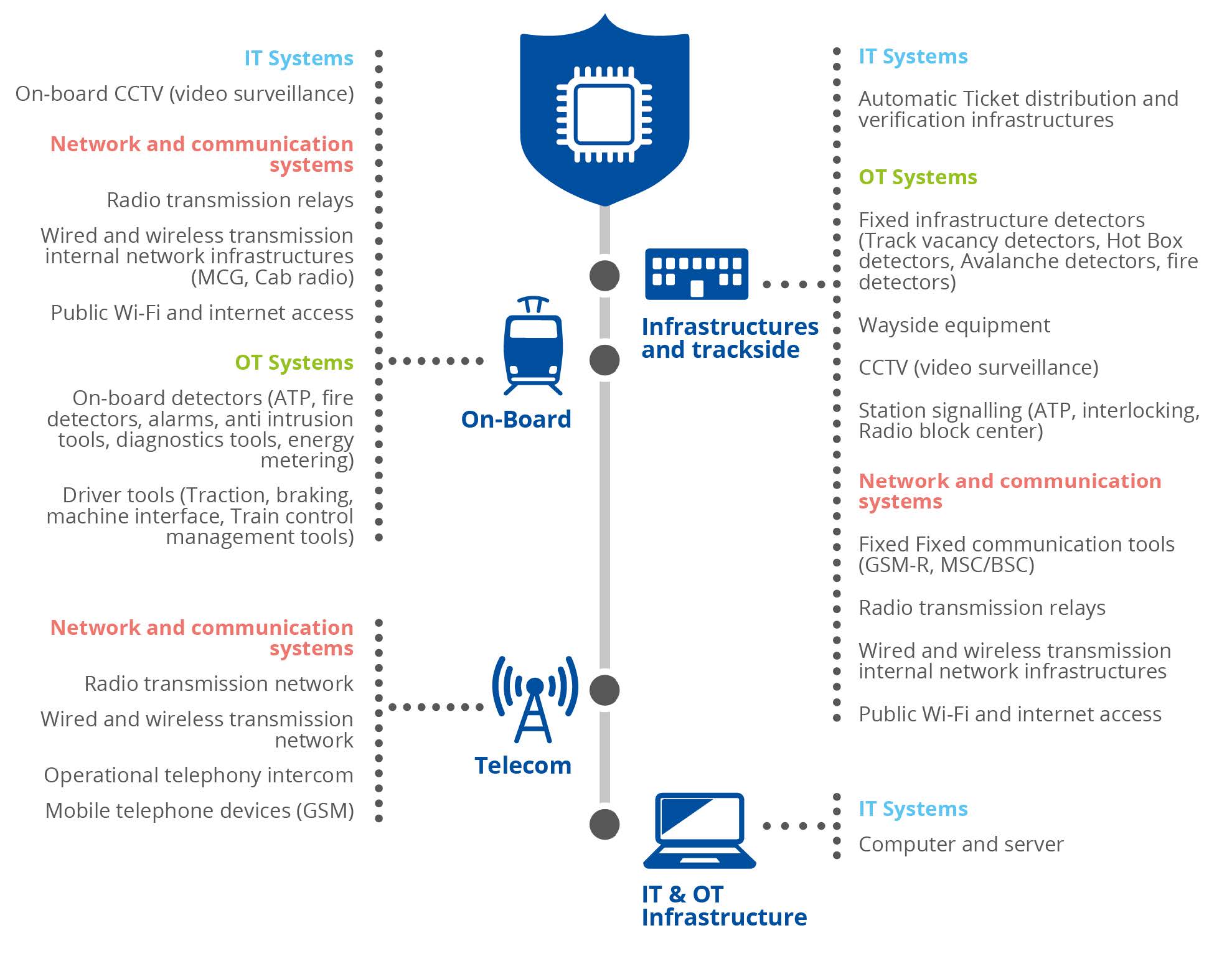
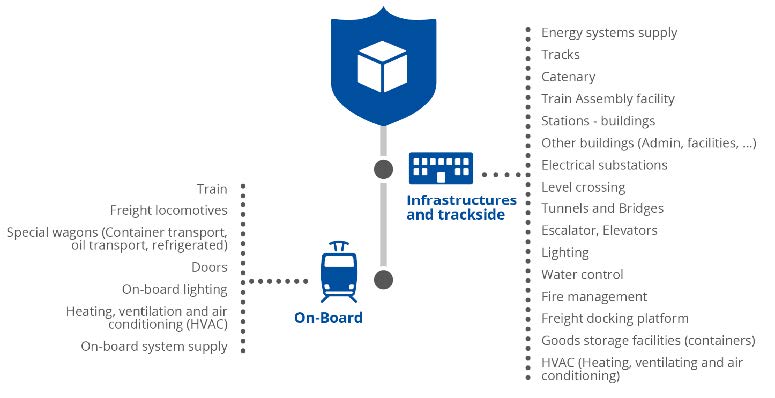
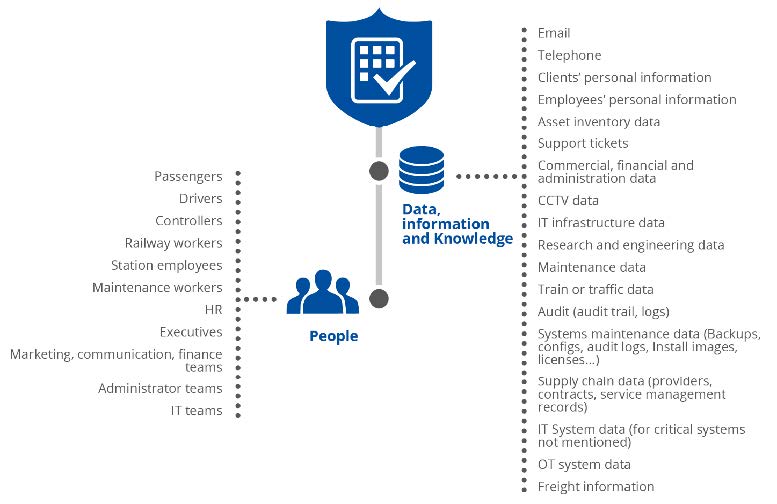
In the railway sector, compromised OT systems can affect passengers’ safety, cause a train accident, or interrupt traffic. OT systems are usually more vulnerable than IT systems, in part due to a lack of cybersecurity awareness in OT personnel, in part because they were not designed with cybersecurity in mind (long lifecycles of 30 years, presence of legacy systems) and because they are less controlled and decentralised compared to IT systems.
While in the past they remained less exposed, often isolated from internet and other IT networks, they are now more and more interconnected with classic IT systems, which makes them even more vulnerable and exposed to cyber threats.
RUs and IMs need to identify which cyber threats are applicable to their assets and services. One of the common questions is whether threats, such as disasters, physical attacks, or outages, should be included or considered as not being specific to the “cyber” ecosystem. Most stakeholders include them, as they can affect information security.
If they are not included, they should be considered in other risk management or business continuity management processes of the company, and this must be agreed on when the threat taxonomy is being developed. Another challenge faced by the railway sector is assessing the likelihood of a threat scenario. One would need to consider the level of capability required for an attack, the level of exposure of the targeted asset, and the intent of an attacker, all of which are information that RUs and IMs may have difficulty in assessing accurately.
Several methods are proposed by the different cyber risk management frameworks. For example, X2Rail-314 proposes to rely on the Common Vulnerability Scoring System (CVSS). They have selected four CVSS Exploitability metrics in CVSS: Attack Vector (System Exposure), Attack Complexity, Privileges Required and User Interaction. Levels for these metrics have been defined, mathematically calculating the resulting likelihood.
Other methods are less quantitative, but also simpler to apply, such as ISO27005, which combines the likelihood of occurrence of the threat (low, medium, high), the ease of exposure (low, medium, high) and the value of the asset (from 0 to 4) to calculate the likelihood of an incident scenario15. It is also very difficult to maintain this information because it changes through time as the threat landscape evolves.
Finally, the railway sector faces challenges associated with supply chains. Security risks related to suppliers (e.g., remote access to the railway networks/systems) are less covered because of the heterogeneous and broad nature of the supplier landscape, but also because stakeholders do not have much control over the cybersecurity level of their suppliers and the cyber risks they may introduce. This topic can be reinforced by making an inventory of all the suppliers, categorising them in term of criticality (e.g., do they have access to a critical system, is there a strong interconnection between systems, do they manipulate sensitive data, etc.) and assessing the cybersecurity maturity of the most critical suppliers as a starting point.
Cyber Risk Scenarios
Scenario 1 – Compromising a signalling system or automatic train control system, leading to a train accident
This scenario requires high motivation of the attacker and in-depth knowledge of railway systems and networks. It is considered a low likelihood scenario. It has been included as the potential impact can be very high and this is one of the primary concerns of railway stakeholders when considering cyber risks. A similar incident took place in the city of Lodz, Poland in 2008 when an attacker managed to hack into a tram system.
Scenario 2 – Sabotage of the traffic supervising systems, leading to train traffic stop
This scenario is a targeted attack using a specific Industrial Control System (ICS) malware to disrupt the traffic supervising systems, thus leading to an urgent stop of train traffic. Such an incident has not yet occurred in the railway sector. This scenario could also be applied to freight docking systems, and thus disturb or interrupt freight activity.
Scenario 3 – Ransomware attack, leading to a disruption of activities
In 2021, ransomware attacks are considered the top threat scenario and are targeting the transport sector. In this case, the attacker infiltrates the information system, exploits a vulnerability, and deploys a ransomware on a large amount of assets. A similar incident happened in May 2017 when Germany’s Deutsche Bahn rail infrastructure was infected with WannaCry ransomware22, leading to messages appearing on station information screens.
Scenario 4 – Theft of clients’ personal data from the booking management system
This scenario is a targeted attack, where the attacker steals the identity of an administrator and is therefore able to connect to a cloud-based booking management system and exfiltrate customer data. A similar incident happened in November 2017 with Rail Europe North America (RENA) suffering due to a 3-month long data breach23 and in January 2019 when China Railway’s official online booking platform suffered a massive data breach, with information later being sold on the dark web.
Scenario 5 – Leak of sensitive data due to unsecure, exposed database
This scenario is also related to data leakage, but the starting point here is a supplier with a low cybersecurity level. The attacker uses this third-party weakness to exfiltrate sensitive data. A similar incident happened in February 2020 with a database of C3UK, which offered Wi-Fi services to passengers in train stations. The database contained 146 million records, including personal contact details and dates of birth, and was exposed online without a password.
Scenario 6 – DDoS attack, blocking travellers from buying tickets
This scenario is a targeted attack, where the prerequisite for the attacker is to have created a botnet network (a set of compromised devices controlled by a hacker to perform their attacks). The attacker can then use the botnet to flood devices with requests and make them unavailable. Another possibility to consider for a DDoS scenario is a non-targeted attack, where an Internet Service Provider (ISP) is targeted with this type of attack, thus affecting railway services that use this ISP.
Scenario 7 – Disastrous event destroying the datacentre, leading to disruption of IT services
This scenario is the consequence of a disastrous event which leads to disruption of activity. The event (natural disaster, fire, etc.), affects the datacentre and destroys part of it, leading to a physical destruction of IT systems and thus a disruption of activities related to these services. Depending on the redundancy strategy of the company (geo-redundancy, cloud, external back-ups, etc.), the disruption can last more or less time. A similar incident happened in March 2021 when OVH27 had a fire in one of its datacentres, making millions of websites unavailable for days.
Conclusions
European RUs and IMs use a combination of good practices, approaches, and standards to perform cyber risk management for their organisations. This report gathers insights on these current practices in a single document and can assist railway undertakings and infrastructure managers in their efforts to apply them. It provides examples of reference material, such as available taxonomies of assets and threats, comprehensive threats scenarios, derived from real incidents and cyber risk mitigation measures, derived by guidelines and standards.
The report also highlights the challenges faced when applying such approaches. Most importantly, there is a lack of a single cyber risk management approach for railway organisations to cover both IT and OT in a unified manner.
IT vs OT risk management approaches. The differentiation between IT and OT in the railway sector is increasingly difficult and having discrete approaches and taxonomies for cyber risk management makes the issue more challenging. In many cases, it can be a complex process to identify which approach is better suited, whether a device can be considered IT or OT or which security measures and which standard should be applied. Having a more structured and unified approach with respect to cyber risk management would help the sector to harmonise, thus facilitating risk discussions between the different entities of the railway ecosystem. It can also enable more collaboration with the supply industry of the sector.
More harmonization and alignment of good practices. Future work could include further alignment of the sector-specific taxonomies and more guidance on the application of good practices. Wherever possible, further standardisation could be pursued, as this is also a request stemming from the railway supply industry, which advocates for more certification schemes at EU level. Significant sectoral challenges remain, including the cyber risk management of supply chains. This could be remedied with a regulatory approach encompassing the entire railway ecosystem under the same cyber risk management requirements. At present, key elements of the railway supply chain, both IT and OT, do not fall under the same European regulatory framework.
Keeping railway systems and cyber risk assessments up-to-date. Another significant issue specific to the sector is the plethora of legacy systems which add an additional degree of difficulty when managing cyber risk. At present, it is not possible to provide relevant recommendations to address the cybersecurity of legacy systems in the railway sector. It would be necessary to involve the railway industry in such an exercise. Additionally, even for newly developed systems, there is the need to ensure that the results of risk assessments remain current, that risks are continuously monitored, and that the security level remains adequate. Maintaining an up-to-date threat landscape for the railway sector could be a step towards this direction.